At the dawn of the year 2024, it has become apparent that top cybersecurity threats have evolved to a dangerous level that is perilous to organizations and individuals.
In 2021, threat actors are believed to have developed the utilization of emerging technologies, notably artificial intelligence, to advance the kind of attacks carried out, making them part of the top cybersecurity threats landscape.
Ransomware has not disappeared as a threat, on the contrary, the attackers continue to focus on critical infrastructure and municipal services, the use of social engineering techniques has become even more insidious and it is becoming increasingly difficult to counter them.
As the level of sophisticated attacks increases, the need for sound security controls and constant monitoring has never been so important to guard against the loss of confidential information and preserve organizational resilience.
The Ever-Changing Nature Of The Security Threat Today
The cybersecurity landscape is undergoing significant transformations, driven by factors such as:
Emerging Cybersecurity Threats: The threat actors are very active and are always in search of new ways and methods to breach organizations’ defenses. This year, ransomware attacks, artificial intelligence attacks, and supply chain attacks are likely to rise.
Technological advancements: What’s happening is that technological advances such as artificial intelligence, quantum computing, and the Internet of Things are bringing in new forms of emerging cybersecurity threats that businesses need to deal with.
Regulatory changes: Analyzing the situation at today’s global level, the government has started to impose even more severe requirements for organizations concerning data privacy rules and regulation and addressing cybersecurity threats in 2024. Failure to do so will attract fines as well as a negative impact on the company’s image.
Evolving market dynamics: The principal trend in the cybersecurity industry depends on changing the focus of cybersecurity tools and moving to a data-driven approach and an integrated cybersecurity environment to combat cybersecurity threats in 2024.
These aspects, mergers, acquisitions, and layoffs therefore depict the cyclicality of the industry.
The Importance of Staying Informed
To navigate this rapidly evolving landscape, organizations and individuals must stay informed about current threats and best practices:
Monitoring threat intelligence: This is primarily to ensure that one is familiar with contemporary threats and their approaches to ensure prevention.
Embracing new security models: Implementation of models such as Zero Trust, DevSecOps, or data-oriented security strategies can benefit an organization in improving its security stance while mitigating new-age threats.
Investing in advanced technologies: The use of artificial solutions, machine learning algorithms, and quantum-safe cryptography solutions will reduce the risks of ever-changing threats and enable programmatic solutions.
Fostering collaboration: Collaboration with private sectors and cooperation and collaboration between organizations and agencies in the government, can enhance cooperation and collaboration in the defense against cyber threats.
Top Cybersecurity Threats in 2024:
- Weaponized AI
- Cloud Vulnerabilities
- Ransomware Resurgence
- Social Engineering Attacks
- Deepfake Technology
- IoT Attacks
- Supply Chain Compromises
- Configuration Mistakes
1. Weaponized AI in Cyberattacks
- Automation of Attacks: As for cyberattacks, AI is used to automate different procedures so that these attacks are quicker and more effective, aligning with the latest cybersecurity trends.
- Enhanced Phishing: Automated phishing may also generate very realistic emails allowing the methods to deceive their intended targets effectively.
- Vulnerability Identification: There are AI algorithms that indicate the vulnerabilities rapidly in systems and so the attackers get to exploit them in a better way.
- Sophisticated Malware: Cyber criminals can also employ AI in the invention of sophisticated malware that automatically changes its pattern in response to countermeasures that are initiated by the defense quadrant.
Implications of AI-Driven Threats on Cybersecurity Strategies
- Need for Advanced Detection Systems: It is important for organizations to implement computational models of threat detection, which are also known as the ability to identify further instances of peoples’ mischievous actions, especially in the context of the latest trends in AI in cybersecurity.
- Robust Incident Response Plans: As dangerous as AI-enabled threats are, they require well-written and constantly updated contingency procedures for the organization’s rapid reaction.
- Employee Training and Awareness: It is imperative to create cybersecurity awareness within the organization’s employees so they can detect and mitigate AI in cybersecurity-intensified risks.
- Continuous Monitoring and Adaptation: This is why organizations must have constant surveillance and change their security strategies according to new threat vectors using AI.
- Collaboration and Information Sharing: Information sharing with fellow players in the industry as well as relevant government agencies improves the overall preparedness against the increasing menace of AI-supported cyber attacks.
By reflecting these points it will allow organizations to be more aware of the adversities of weaponized AI within the Cybersecurity domain.
2. Cloud Vulnerabilities
Higher Rates Of Cloud Environment Intrusions
- 75% Rise in Intrusions: New records forecast a 75% rise in intrusions in cloud environments, thus calling for better security against cloud security threats in cloud computing. Such a volumetric increase is observed due to constantly evolving and more frequent and complex cyber threats posed to cloud infrastructures, further highlighting the importance of addressing cloud security threats.
Abuse of Misconfiguration and Identity Vulnerabilities
- Misconfigurations: Misconfigurations are also a big player in cloud weaknesses where they contribute to about 80% of all the cloud weaknesses. Inadequate security can pose a severe threat to an organization since attackers can gain access, compromise the data, and expose the organization’s secrets. For instance, the storage buckets with wrong configurations would mean that any piece of information is accessible to anyone.
- Identity Flaws: Lapses in IAM put users at risk regarding the compromise of their credentials and unauthorized access. Many of these vulnerabilities serve as gateways through which attackers gain access to information and services in the cloud; therefore, proper authentication should be conducted in organizations, and there should be a general check on permissions.
Some common cloud risks
- Misconfigurations: Misconfigurations of the clutch make the resources publicly available.
- Access Credential Theft: Credentials from stolen accounts enable the exploitation of vulnerabilities usually of phishing or credential squatting.
- Phishing Attacks: Phishing is still a prevalent technique used, so beware from attackers who lure users into providing them access to cloud accounts.
- API Attacks: APIs also can be attacked, which means that an API can be exposed and used for purposes of accessing or even changing data.
- Lack of Visibility: Multiple levels of cloud structures complicate risk visibility and thereby challenge organizational security monitoring and control.
- Insider Threats: This is because employees or contractors who are in a position to use cloud resources can act maliciously, though unconsciously, to create security threats.
- Unsecured APIs: Some APIs are not well protected, therefore, they are vulnerable to being and this will cause leakage of data and unauthorized access.
- Shared Technology Vulnerabilities: If multi-cloud environments are adopted, there are risks of making the frequently used substrate components weaker, thus making the environments prone to attacks.
- Serverless Architecture Vulnerabilities: Serverless functions have vulnerabilities that expose confidential data and also affect performance.
Implications for Cybersecurity Strategies
To address these vulnerabilities, organizations should adopt comprehensive cloud security strategies, including:
- Regular Security Audits: Regularly scanning its cloud configurations with the specific purpose of detecting other misconfigurations.
- Enhanced IAM Practices: Enhancing the policies on identification of users and role of access control together with the use of MFA.
- Continuous Monitoring: Real-time monitoring of cloud computing through various tools that are used in the detection of any irregular activity and perhaps attacks.

- Lightning-fast speeds to browse without lag
- Servers in 105+ countries around the globe
- Military-grade security to stay safe online
- Try it risk-free with its money-back guarantee
- Native apps for all major devices

3. Ransomware Resurgence
Increased Glow of Ransomware Attacks
Ransomware attacks have come back in force in 2023 after a slight dip in 2022. Mandiant learned of about a 75 percent increase in posts on data leak sites and about a 20 percent increase in ransomware investigations.
More than fifty new ransomware families and variants were identified, which paved the way for new top cybersecurity threats like ransomware evolution.
The use of legitimate tools has been increased by the attackers for successful intrusions while ransomware is delivered quickly, often in less than two days.
They have affected victims from more than 110 countries which gives a clear illustration of how this cyber threat is universal.
Risk arising from the increased Ransomware-as-a-Service (RaaS) Models
The new trend in ransomware attacks is the use of the Ransomware-as-a-Service business model in which ransomware developers provide their software and services to other cyber-criminals for a certain percentage of the ransom amount.
This model decreases the entrance threshold for newbies in the world of cybercriminals, who do not necessarily require complex technologies to implement them.
As one of the top cybersecurity threats, the diversification and dynamic evolution of ransomware groups, as well as rebranding and forming of new affiliations, partly predefined the appearance of new variants of RaaS.
For example, ALPHA/BlackCat and LockBit have modified their approaches and remain dangerous to numerous industries.
Average Ransom Demands and Its Effect On Companies
However, in the context of the financial consequences of ransomware, statistics remain rather high — in 2023, adversaries received more than $USD 1 billion from victims. The average value of these demands has risen because these attacks proved to be lucrative and, therefore, satisfactory.
This paper also highlights that organizations are not only units to be held financially liable for the cost of ransom paying but also may suffer drawbacks in the future such as organizational contamination, operational interferences, legal responsibilities, and ramifications of their images.
The use of data encryption as well as sensitive data blackmail has evolved to be a standard strategy, where the perpetrator uses the two to apply pressure to the victims, in a bid to compel them to pay the ransom.
Consequently, the rising ransomware in 2023, one of the top cybersecurity threats, is advising organizations to improve their cybersecurity posture.
Conduct further refinement in their incident response plan, and remain wary in today’s sophisticated and ever-changing cyber threat environment.
4. Social Engineering Attacks
Phishing and Impersonation remained the most extensive type of cyber threats in the state.
Two of the most common techniques of using people’s weaknesses by hackers are social engineering strategies, such as phishing and impersonation.
A prime example of a social engineering attack, phishing scams, special forms of online fraud aimed to lure people into divulging their details on-website, in emails, or messages – represent 98% of all cybercrimes.
In this category, spear phishing, where the attacks are focused on particular individuals or organizations, has been very effective with 95% of successful network penetration using it.
The element of false trust and false sense of urgency incorporated in such an attack makes them highly successful since the attackers pretend to be people or organizations that the targets would naturally trust.
Counts of How Effective Social Engineering Is
The effectiveness of social engineering tactics is underscored by several alarming statistics:
It was also seen that 75% of targeted attacks begin in the email, hence underlining the importance of phishing to kick-start cyber incidents.
CEOs receive an average of more than seven hundred social engineering attacks per year suggesting the high prevalence of this threat.
AP, a study on the different types of phishing attacks revealed that eighty-three percent of the enterprises in the U. S have been targeted by phishing attacks.
It was discovered that the mean cost per social engineering attack was about $130,000, hence signifying the fact that these types of cybercrimes are not only severe but also costly.
It was shocking that 90% of the data breaches exploited the weakness of the people, proving the fact that the human factor is still a critical weakness in the efforts to enhance cybersecurity.
These statistics therefore clearly indicate the need for organizations to ramp up their cybersecurity-related education and sensitization to contain risks posed by social engineering attacks.
When businesses know what tactics their adversaries are applying and create awareness on this issue there is a high possibility of avoiding being attacked by cybercriminals.
5. Deepfake Technology
Deepfake technology which enables a machine to superimpose one face onto another person’s body and lip-sync their words has been on the rise in the recent past.
Such manipulations created by AI are gradually turning into an instrument for the propaganda of false information to the population about the media and communication.
Some notable examples include:
An example of this is the fake deepfake video of Ukrainian president Volodymyr Zelenskyy in late March 2022 calling on his soldiers to lay down their arms, which was an obvious fake.
Before being flagged as fake, one would see deepfakes of British Labour Party Leader Keir Starmer and the leader of the Slovak opposition party.
Scam calls purported to be from the U. S. President Joe Biden and produced using artificial intelligence called people in New Hampshire’s Democratic primary not to vote.
But before that, in early 2019, a notorious deepfake video was spread throughout Malaysia that seemed to depict the country’s Economic Affairs Minister in a compromising position; he and his supporters claimed that the video was fake.
Potential for Deepfakes to Disrupt Trust in Media and Communications
What is even more problematic is that deepfake technology is evolving at a very fast pace, making any kind of digital media manipulation rather easy to achieve.
This is the case because convincing fake content can be created in such a way that it seems to originate from trusted sources, which will considerably erode the public’s trust.
Some key concerns include:
Both authoritarian and democratic states can use deepfake technology to interfere with election campaigns and bend political discussions with deepfake propaganda.
Deepfakes and impersonation of the public today figures for finance frauds and scams
The production of revenge or non-consensual deepfakes which have been employed in harassing politicians including Aimee Hunter of the Northern Ireland Assembly.
Fake news that researchers are unable to dispel because most people are skeptical of information found on the internet and AI-produced fake news doesn’t tend to go viral
Though the use of deepfakes is not necessarily unlawful per se, it can fall foul of laws on pornography involving persons under the age of 18 years, defamation,n or incitement to Discrimination.
Attempts have been made to create deepfake detection tools and blockchain-hashed systems, but the dangers remain persistent since the development of AI tools continues at a breakneck pace.
Finally, deepfake manipulation adds to the list of threats to the information ecosystem; This threat can only be fought off using a multi-faceted strategy that seeks to include developing technology that is resistant to hacking and energy.
Legislation, raising awareness and the constant promotion of integrity in media and communication systems in this age of the world.
6. IoT Attacks
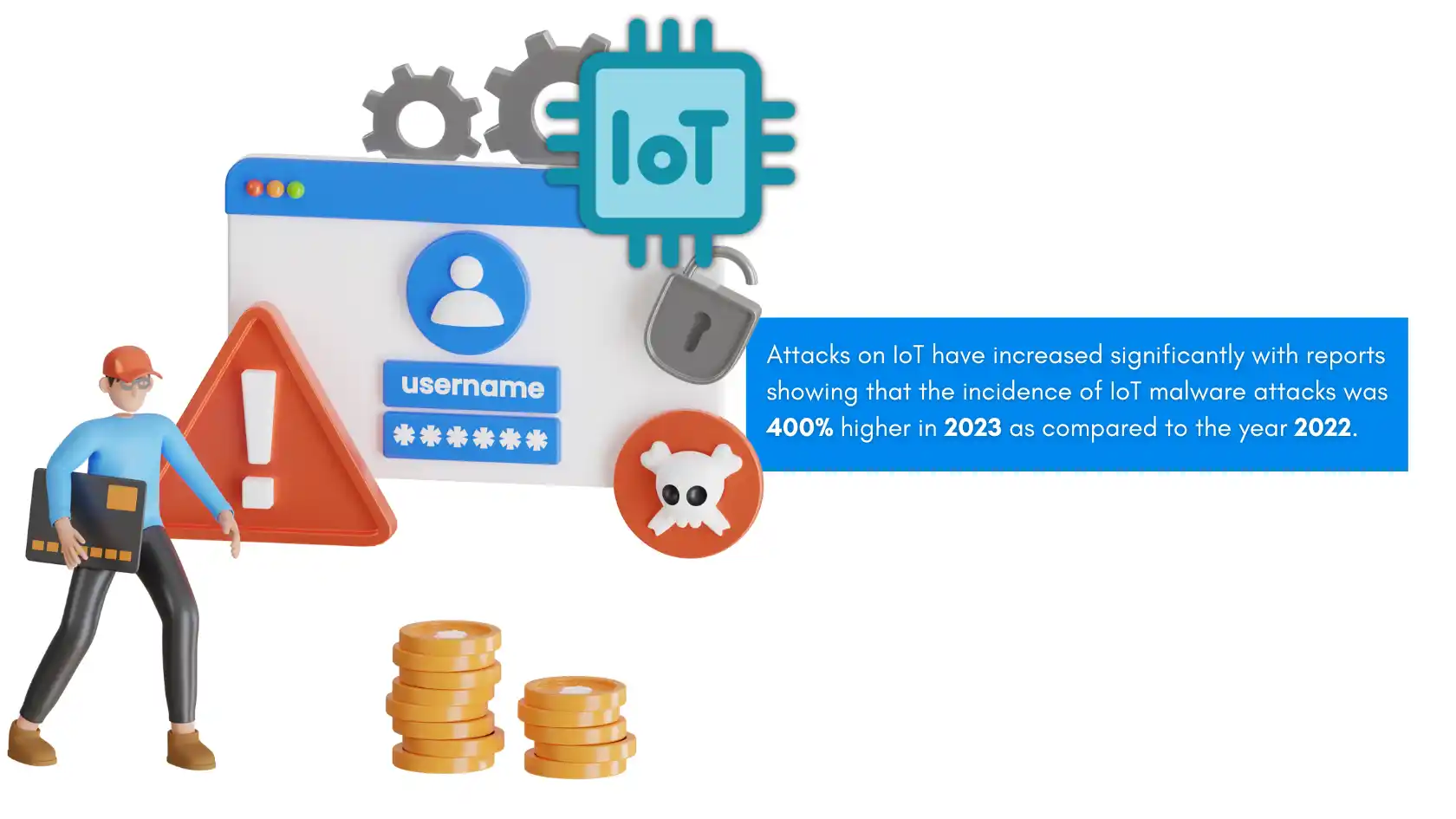
Greater Focus on the Internet of Things (IoT) Device
Attacks on IoT have increased significantly with reports showing that the incidence of IoT malware attacks was 400% higher in 2023 compared to the year 2022.
This increase can be attributed to the increased usage of IoT devices across industries such as manufacturing, education, security, and smart homes among others.
Thieves are actively using the opportunities opened by these devices because most of them have weak protection due to their integration of many functional facilities, highlighting the critical need for enhanced cybersecurity in IoT devices.
For instance, manufacturing firms have experienced 6,000 IoT malware attacks in a week, making it clear that IoT vulnerabilities are among the top cybersecurity threats.
Challenges and Risks Linked With Smart Apparatus in Homes and Commercial Premises
IoT devices are particularly susceptible to a range of vulnerabilities, including:
- Inadequate Authentication: It is also a known fact that very few IoT devices support strong authentication and thus the field is open to attackers, contributing to the top cybersecurity threats.
- Misconfigurations: The unsecured devices themselves can leak data and create numerous openings for hackers.
- Legacy Vulnerabilities: Most IoT devices are powered with software that has reached the end of life meaning it is vulnerable to various attacks.
- Lack of Encryption: IoT devices communicating with other IoT devices use open-air routes hence the information transmitted can easily be captured and altered.
- Botnet Formation: The affected IoT devices can be collected to form botnets that are then deployed for DDoS purposes whereby the targeted systems and services are flooded.
- Physical Security Risks: The IoT devices are typically located in insecure settings and usually available to the public; they are hence prone to physical manipulation and real assaults.
The top cybersecurity threats posed by IoT are only likely to increase in scope as more and more devices connect to the Internet and broader society.
Due to poor protection from hackers and terrorists and the ever-evolving, complex risks that are associated with IoT devices, protection from those threats requires constant surveillance and amendments, as well as the reinforcement of security measures.
This is why organizations and individuals must ensure the security of their IoT environments as they seek ways of addressing these vulnerabilities.
7. Software Supply Chain Threats:
The threat landscape for software supply chain attacks is becoming increasingly dire, with reports indicating a dramatic rise in these types of attacks:
- According to the report made by a leading research company Gartner, software supply chain attacks had increased by triple digits.
- Last year’s Ponemon Institute study revealed that 59 percent of organizations have reported supply chain attacks, and 54 percent of them occurred in the past twelve months.
- Sonatype’s report pointed to the phenomenal average of 742% annual growth of the software supply chain attacks within the past three years.
Several factors contribute to this alarming trend:
- Modern malicious actors are more aware of software components and libraries making it easy for them to exploit the weaknesses in the software.
- Visibility of the software is poor mainly because; many organizations have no way of counting the software they use and have no clue if there is a vulnerability in the software.
- New threats come from third-party and open-source components; the latter are also usually full of different unresolved vulnerabilities.
Third-party vendors’ security and Open-source software.
The reliance on third-party vendors and open-source software is a critical area of concern:
- This was revealed from the study conducted by ReversingLabs highlighted that Malicious packages in the open-source repository increased by 28% in 2023.
- According to Revenera’s research, 64% of businesses had experienced supply chain attacks because of the rising use of open-source software solutions.
To mitigate these risks, organizations must adopt robust security measures, including:
- Application discovery and mapping to get an understanding of the nature of applications and their interconnections and, therefore, to be able to identify existing risks.
- Third, performing periodic security assessments of third-party components and the assurance of code signing and code verification to reduce the risks of malicious code compromise.
- Measures that allow them to respond immediately to any security threats that may affect their software supply chain.
Due to the ever-changing cyber-threat landscape, application software and third-party vendors must be protected. Thus, organizations need to make themselves more recognizable and actively counter such threats as they ramp up in complexity.
8. Configuration Mistakes
Finally, there is security misconfiguration which stands for weak security settings where systems are set up inappropriately, and they are liable to be hacked.
These misconfigurations may be caused by such factors as human mistakes, ignorance of security measures, or forgetting to upgrade a software system. Here are some of the most common types of security misconfigurations:
Default or Weak Passwords: By default, it is common to find systems with a default password that is not changed by the end-user during the setting up of the system. Passwords that do not come up to a security standard are also very dangerous as well. The last vulnerability is the use of weak passwords.
Improperly Configured Databases: The major risk lies in the fact that the databases often have weak or very liberal access rights or are available on the internet in a way that requires no login, thus providing open access to restricted data.
Unsecured Cloud Storage: Socially stored data is not secure as it loses scalability if not properly configured while access controls can be unprepared or data not encrypted.
Misconfigured Firewalls and Network Settings: Lack of proper setting of firewalls makes it possible for months or maybe years for hackers to access all the ports, thus compromising your information.
Outdated Software or Firmware: Lack of patching and updating applications leaves systems open to known attacks because hackers do look for unpatched systems.
Unprotected Files and Directories: Those files and directories that do not have well-implemented security policies and controls could be manipulated by attackers to get access to confidential data and or system functions.
Human Error: Some of the misconfigurations are caused by negligence on the part of the system administrators including; not following security policies and not reviewing the access permission.
Emerging Findings Relating to the Even Distribution of Exploitable Misconfigurations
The prevalence of exploitable security misconfigurations is alarming:
- From the Verizon Data Breach Investigations Report released in 2022, it was agreed that misconfigurations made up more than one-fifth of the data breaches.
- World’s most renowned list of web application vulnerabilities revealed that security misconfiguration is the fifth most dangerous risk; more than ninety percent of applications revealed some form of misconfiguration and 4% is the average incident rate.
- A survey revealed that these days 73% of organizations have at least one severe security misconfiguration which puts the organizations’ sensitive data at risk.
Recent News Showcasing New Threats Of Cybersecurity In 2024

Uninterrupted, high-speed browsing, zero logs so your online activity is always private.
Over 7000 people checked out NordVPN in the last month
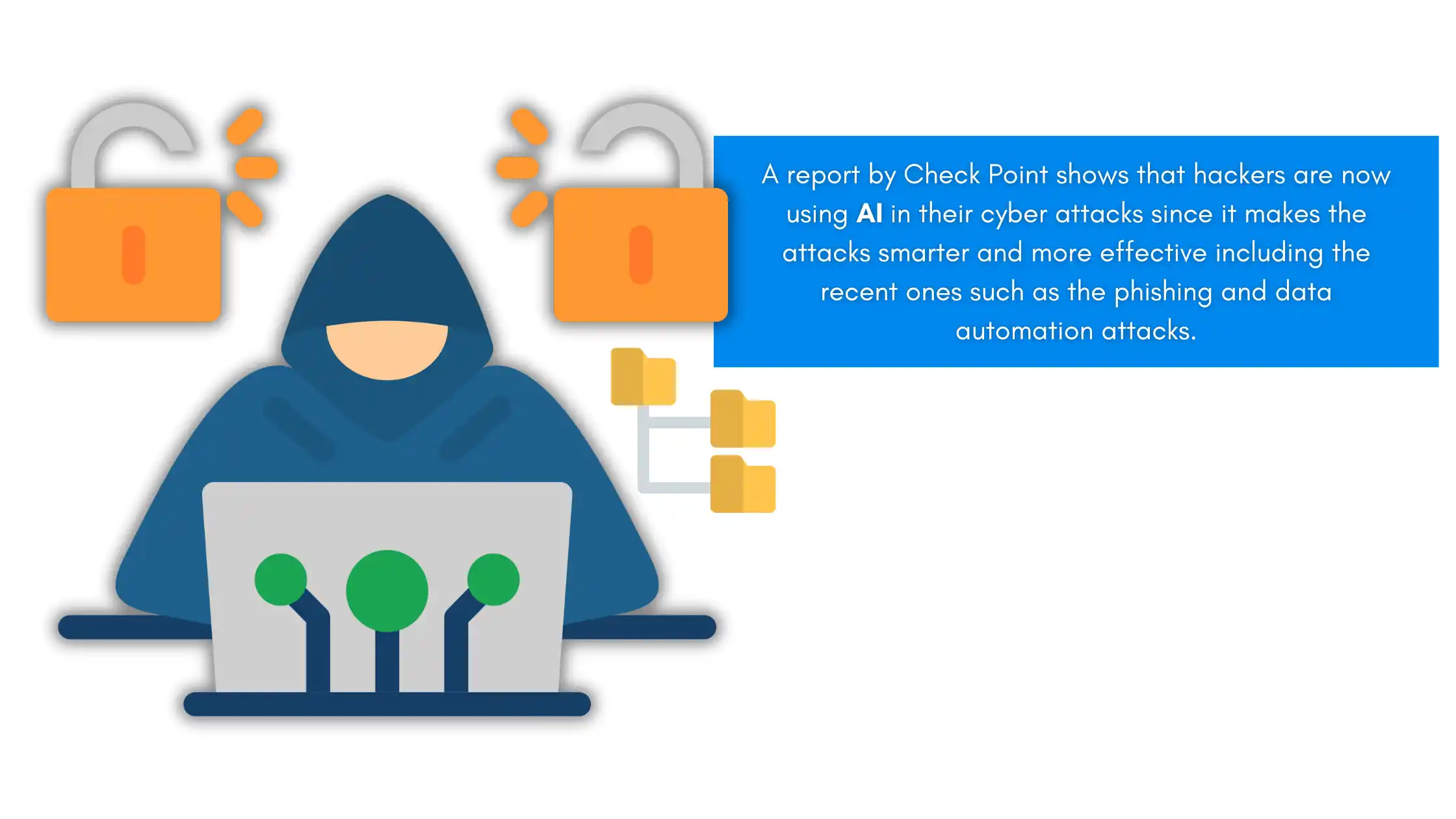
Weaponized AI is now a new norm in CYBER ATTACKS
A report by Check Point shows that hackers are now using AI in their cyber attacks since it makes the attacks smarter and more effective, including the recent ones such as phishing and data automation attacks.
This trend is apt to rise to the next level in 2024 because AI-driven threats will emerge as one of the top cybersecurity threats of the new generational threats.
A Splashtop survey released found that 35 percent of the CISOs are currently implementing AI in security solutions, and a further 61 percent intend to do so in the next year.
But, 39 percent of the CISOs also said they would educate their teams on the risks of generative AI, which is becoming one of the top cybersecurity threats to address.
Cloud vulnerabilities are often targeted by various cyber criminals.
Recently, the attacks on cloud environments have increased by 75% owing to the misconfiguration and Identity weaknesses in the hybrid and multi-cloud infrastructure.
This trend is rather worrisome given a time when organizations increase their dependence on cloud services.
According to a report published by Embroker, it was noted that 82% of data breaches in the year 2023 involved data that was stored in the cloud, and this was threatened by ransomware.
It also discovered that 84 percent of cloud-conscious intrusions were likely eCrime actors.
The authors considered it potentially high since 43 percent of such likelihoods had been reported by earlier surveys.
FAQs
What is the worst Cyber Security threat in 2024?
In what way are cloud vulnerabilities an issue in 2024?
What is the probability of a ransomware attack in the year 2024?
In what way will deepfake technology be a threat in 2024?
Conclusion:
Consequently, the state of cybersecurity in the year 2024 is characterized by issues such as weaponized artificial intelligence, cloud security risks, and most especially, ransomware attacks.
As these are among the top cybersecurity threats, organizations have to keep their guards up, constantly make changes to their security measures, and pay for good security to counter these threats and ensure cybercriminals cannot lay their hands on the organization’s sensitive information.






