Everyone at some point or another has to have pondered on how they could contribute to the making of the Internet safer. Meet blockchain in cybersecurity – the prospects of which are already opening up new opportunities in the sphere of protecting online spaces. Now that we’ve established that blockchain is a thing and is possibly transformative, what is it, and how does it do that?
What Is Blockchain
Blockchain is a decentralized database that contains information shared through a mechanism that is very hard to manipulate. It operates like a book where each page is connected with the previous and next pages, and there are many copies of this book stored on different computers all over the world. That’s the way blockchain operates a little!
Blockchain was first introduced in 2008 and launched in January 2009 as a payment system for a new digital currency called Bitcoin, created by an unknown person or group under the pseudonym Satoshi Nakamoto. Since then, the application of blockchain has expanded well beyond simply being about digital money due to the attribute of being decentralized. It is now stirring up many industries, and actively contributing to protecting our Internet space.
Do You Know?
The first time that Bitcoins was actually used to trade real merchandise was in 2010 when a programmer from Australia used Bitcoins to purchase two pizzas. The pizzas that had purchased cost 10,000 Bitcoin today it is equal to millions of dollars.
Blockchain is socially related to a broader notion, which is decentralization. Distributed systems are a far cry from the kind of centralized system in which a single power holds the reins. In contrast, power is distributed among many subjects.
This approach is relevant when it comes to securing internet connection because it can prove really hard for the undesirables to organize themselves and their intentions toward the system. Understanding what is blockchain is essential to grasping the advantages of this decentralized approach.
Characteristics of Blockchain
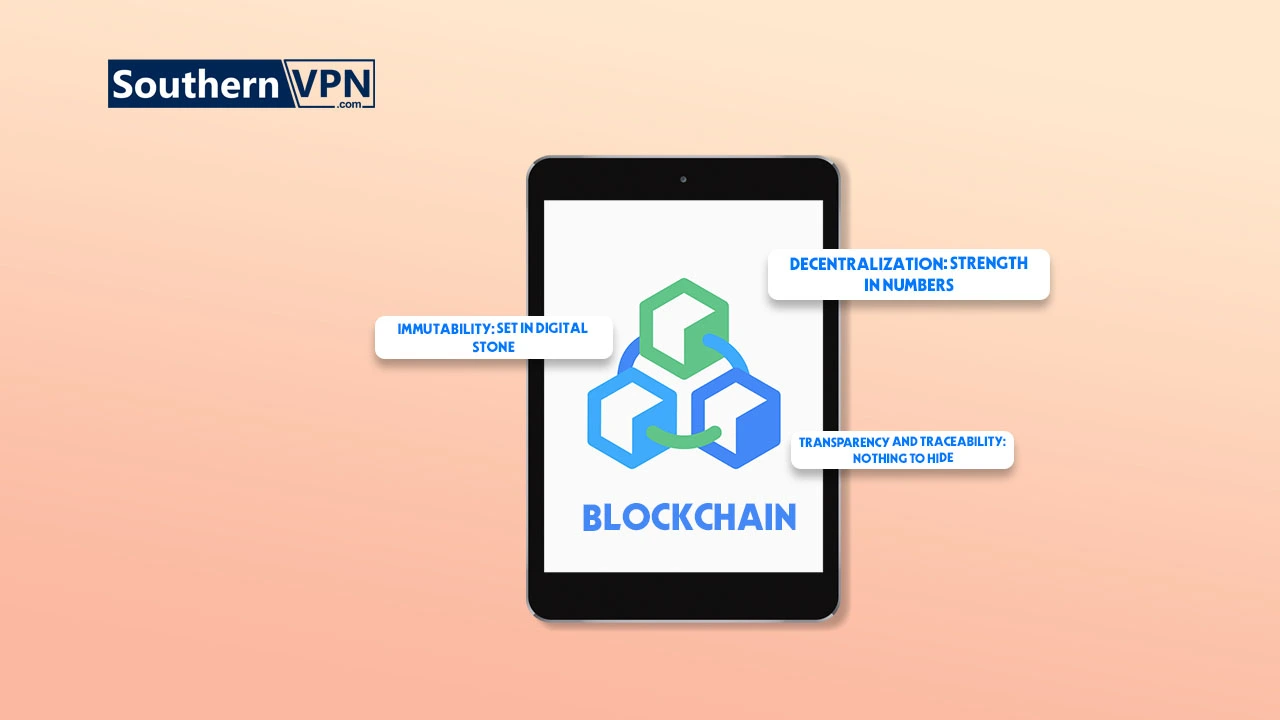
Now, let me explain further the points as to why blockchain is indeed very useful especially when it comes to protecting data on the Internet. The key features of blockchain are decentralization, immutability, and transparency. Decentralization distributes information across a network, making it hard to manipulate.
Immutability ensures that data, once entered, cannot be altered. Transparency allows real-time tracking of transactions and activities, enhancing security.
Blockchain enhances online security through decentralized data storage, making it hard for undesirables to manipulate information. It uses cryptography to secure data and ensures transparency and traceability, which are powerful tools against fraud and unauthorized access.
Decentralization: Strength in Numbers
What is happening, do you remember that we stated that a blockchain is like a book that is kept on several computers? That’s decentralization in action. Compared with the way of centralizing the distribution of information, it distributes information through a network with the aim of excluding the situation that there is a weak link.
Slightly it is like photocopying most of our important papers and documents, and where in case the original papers are either lost or destroyed, the photocopies act as our standby. This decentralized approach is crucial for both blockchain and cybersecurity, as it ensures data protection and integrity.
The decentralized approach has a significant effect on data accuracy and openness. It is difficult for an individual to manipulate the information because many people have copies of the same information and therefore, if an individual wanted to change the data sneakily, nobody will notice. This feature is particularly important in the realms of blockchain and in any comprehensive cybersecurity guide.
Immutability: Located in the Digital Stone
They are irreversible once entered because modifying or erasing data in a block affects the variances of the chain. Immure, just as writing in ink, rather than in pencil, once information has been written it cannot be erased. It utilizes cryptography – a field of math that converts data into a very difficult to decipher code. Any attempt made to alter even a smallest part in the information converts the code entirely, and informs everybody about the attempt.

- Lightning-fast speeds to browse without lag
- Servers in 105+ countries around the globe
- Military-grade security to stay safe online
- Try it risk-free with its money-back guarantee
- Native apps for all major devices
Pro Tip
When choosing blockchain-based services, look for those with a large and diverse network of participants. The more spread out the network, the more secure it tends to be.
Transparency and Traceability: Nothing to Hide
Blockchain allows for real-time tracking of transactions and activities. This transparency is a powerful tool against fraud and unauthorized access. Imagine being able to see every step of a package delivery or every change made to an important document. That’s the kind of visibility blockchain can provide.
Do You Know?
Some countries are exploring blockchain for voting systems to ensure election integrity and transparency.
| Feature | Traditional Centralized Systems | Blockchain-Based Systems |
|---|---|---|
| Control | Full control by a central authority | Control distributed among users |
| Security | More vulnerable to single points of failure and attacks | Enhanced security through decentralization and cryptography |
| Data Integrity | Data can be altered or deleted by the central authority | Data is immutable and tamper-proof once recorded |
| Transparency | Limited transparency; data access controlled by authority | High transparency; all transactions are publicly verifiable |
| Response to Threats | Reactive measures to security breaches | Proactive measures through consensus algorithms |
| Anonymity | Users are typically identifiable | Offers greater anonymity for users |
| Cost of Security | Often high due to the need for extensive cybersecurity measures | Potentially lower due to reduced need for intermediaries |
This table highlights the key differences in security features between traditional centralized systems and blockchain-based systems, emphasizing the advantages of blockchain in terms of security and data integrity.
Application of Blockchain in Enhancing Security
Now let us discuss the means by which blockchain is proving to enhance the prospects of online security.
Identity Management: You Are What You Claim to Be
Perhaps, one of the most promising uses of blockchain in connection with Internet security is associated with the idea of the management of our personal identities. Blockchain and cybersecurity allow what is referred to as the self-sovereign identity systems. A self-sovereign identity system in blockchain allows users to have more control over their personal identity data and how it is used on the internet.
It enables users to prove their identity while only providing relevant information, thus enhancing privacy and reducing the risk of identity theft.
Blockchain-based methods in identity management allow the user to prove his/her identity while providing only relevant information. Just as you do not need to provide your home address when ordering a beer for your 21st birthday, the same fashion, one does not need to provide personal details when voting and exercising his or her right in a democratic country.
Such an approach to handling identity also aids in avoiding identity theft and, thus, improves the privacy of users. Think about the possibility to fill in an application for a loan, to complete the registration form for a particular service or to vote on the Internet and not to be concerned about the protection of your personal information.
Pro Tip
In the future, watch for developments in blockchain as a potential solution for managing identity. It could present a safer means of hosting your presence on the internet.
Smart Contracts: Cutting out Middle-man
Smart contracts are self-executing contracts with the terms of the agreement directly written into code. They automatically execute actions when predefined conditions are met, eliminating the need for intermediaries and enhancing security and efficiency in transactions.
Here’s a simple example: suppose you are selling your car. A smart contract can meanwhile have a programmed clause to transfer the ownership to the buyer once a certain amount of money has been received into your account. No intermediary, third party who will divide the focus of the deal, and no possibility for last day deal cancellation.
Smart contracts are being used in various industries:
- In finance, they are helping with mechanical procedures other than clearing and settling of shares while at the same time minimizing cases of fraud.
- In supply chains, they’re are safeguarding of the supply chain information and details of product from the manufacturer to the end consumer.
- In real estate, they are cleaning up deeds and contracts of real estates and trying to cut down on papers as much as they can.
Do You Know?
Now there are many insurance companies that decided to take a shot at smart contracts in order to streamline and almost instantaneously process claims and subsequently payouts which can take from 7 to 14 days and sometimes even more.
Secure Transactions: Removing the Intermediary
Blockchain makes it possible for individuals to directly engage in transactions with one another by eliminating the middlemen such as banks. This is evidenced perhaps by products such as Bitcoin and other virtual currencies but it is not limited to that.
By using blockchain for transactions, we can:
- Reduce transaction fees
- Speed up transfer times, especially for international transactions
- Increase security by eliminating the need to trust a central authority
Challenges and Limitations
However, it is also important to point out that despite making a massive contribution to online security through blockchain, it comes with a set of certain problems. Understanding the impact of blockchain is necessary to learn these restrictions, apply blockchain technology in the proper ways, and minimize the risks.
Potential Vulnerabilities: No Fort is Impregnable
Another famous type of blockchain risk is the “51% attack. ” A 51% attack occurs when a participant or group of participants in a blockchain network controls more than 50% of the network’s computational power. This allows them to manipulate recent transactions and potentially disrupt the network. While difficult and expensive to execute, it poses a significant security risk.
Pro Tip
When using blockchain for money stuff, pick popular networks that lots of people use. These are safer because they’re harder for bad guys to attack. Some people might not like this advice, but it’s still a good idea for safety.
Scalability Issues: Growing Pains
The problem is that as it expands the blockchain networks which are involved in the management and storage of various transactions can slow down. Blockchain faces scalability issues as the network grows, potentially slowing transaction times and increasing costs. Solutions like sharding, which divides the network into smaller segments, are being explored to address these challenges and improve efficiency.
Do You Know?
There are some new generations of blockchain platforms that are working to find efficient solutions in order to cope with scaling problems like sharding means dividing the network into small segments.
The Myth of Invincibility
Before proceeding with the consideration of blockchain, it is crucial to state that it has added immense levels of security to online environments but is not invulnerable to cyber threats. As with any technology, there is always the possibility of software bugs or implementation issues, or new vectors of attack.
In my opinion, the use of Blockchain for online security is well-aligned, it is a comprehensive solution, but not a one-size-fits-all solution.

Uninterrupted, high-speed browsing, zero logs so your online activity is always private.
Over 7000 people checked out NordVPN in the last month
Future Outlook of Blockchain in Cyber Security
Future trends in blockchain technology include the development of quantum-resistant blockchains, improved interoperability between different blockchains, and the creation of privacy-enhancing technologies for private transactions. These innovations aim to enhance security and broaden the application of blockchain across various industries.
Ongoing Innovations: The Only Thing That Remains Is Change
Blockchain technology is growing in the twin process of continuous expansion through a ballooning number of applications and constant improvement. Some areas to watch include:
- Quantum-resistant blockchain: With a progression of quantum computing, the scholars are thinking of a blockchain system that is defenseless against attacks from quantum computers.
- Interoperability: Maybe, in future blockchains, there will be improvement of the interaction between them with a particular focus on blockchain security.
- Privacy-enhancing technologies: There are new technologies that are being created competently to make private transactions possible in public ledgers.
Pro Tip
Blockchain technology is rapidly evolving so continually read relevant tech news and join discussion forums about blockchain.
Integration Across Sectors
Many experts believe that blockchain security’s influence on online security will continue to extend to other industries in the coming years. We may see increased adoption in areas like protecting internet privacy:
- Healthcare: When discussing medical records it is important to share that information securely while at the same time protecting the privacy of the patient.
- Education: Proper documentation of the years of training and education that cannot be forged.
- Internet of Things (IoT): Better protection of the several billions of IoT devices that are currently in homes and cities.
Do You Know?
Now some countries are piloting the application of blockchain to protect official documents and deliver digital services to people.
Collaboration is Key
In essence, the realization of Blockchain’s full potential in improving the international dimension of cyber security requires collective efforts. This includes:
- That is why organizations implementing blockchain solutions and discussing their experiences
- Existing technology providers coping with these issues and going on to explore how these problems can be solved.
- Sustaining innovation and users’ protection have emerged as major objectives of regulatory bodies to develop necessary frameworks
- Schools and colleges introducing blockchain security in their curriculum to produce capable cybersecurity experts of the future
Common Misconceptions about Blockchain: Myths and Facts

Common misconceptions about blockchain include the beliefs that it is only used for cryptocurrencies, is slow and inefficient, is unhackable, is anti-government, and is completely anonymous. In reality, blockchain has diverse applications beyond finance, can be efficient in specific contexts, is not entirely hack-proof, is being explored by governments, and offers transparency with privacy options.
Myth
Blockchain is applied in just one application, which is cryptocurrency.
- Myth: Today, it is mostly used for Bitcoin and other cryptocurrencies.
- Fact: Blockchain came with Bitcoin; however, it is not restricted to financial purposes only; blockchain can be incorporated in the supply chain, identity, voting, digital identities, among others.
Blockchain is slow and incompetent
- Myth: As earlier noted, blockchain technology is slow and less efficient as compared to the other technologies.
- Fact: Other types of public networks are slow because they are based on the distributed ledger technology as in the case of Bitcoin and Ethereum. This is, however, applicable to public or open blockchains while private/permissioned. blockchains that are developed for specific applications are much faster and very efficient.
Blockchain is unhackable
- Myth: Blockchain cannot be hacked because it is not operated under the regulation of one authority and all transactions that occurs on the block chain are coded.
- Fact: However, with blockchains, the ability of the wrong persons to get or change the data further becomes very difficult, although blockchains are not hack proof. When the historical reference is stored off-chain or when the data is in the format of a part of private/permissioned blockchain it is prone for forgery or alteration by the administrator.
Blockchain is anti-government
- Myth: All in all, one can state that blockchain is intrinsically anti-government and is designed to actively diss the Institutions.
- Fact: As one of the major components that contribute to the creation of decentralized networks, blockchain is not anti-governmental by its nature. Today, a significant number of governmental bodies and companies are looking for the existence of the potential of applying blockchain technology.
Blockchain is completely anonymous
- Myth: Another fascinating feature is that blockchain transactions are absolutely anonymous and impossible to track.
- Fact: For public blockchains, the transactions are transparent but individuals are disguised and their details are represented by numerical sequences in a website.
However, the users can remain anonymous if carefully observing the rules of the network. Private/permissioned blockchains, on the other hand, have limitations on who can join and this is controlled by an organizer.
Facts✅
Blockchain at the present moment partly has numerous network protocols.
- Fact: The blockchains are divided into several groups or types depending on their characteristics and they include the likes of; Bitcoin, Hyper ledger fabric and Ethereum.
Blockchain can be of two categories; BIS Public and BIS Private.
- Fact: Depending on the access rights block chains can be divided into two main groups which are public block chains that give its client unrestricted access to join its network and private block chains that grants network access to its users only when it is requested by an administrator.
Blockchain has associated costs
- Fact: This rides the fact that, although use of blockchain incurs certain one time costs, in the long run it causes drastic reduction of cost; however, it is important to know that operating in a blockchain network has its costs including hardware costs, transaction costs, software costs, and maintenance costs.
Blockchain is a shared record keeping that is maintained across many centers.
- Fact: Blockchain can be described as a distributed ledger system that enables the decentralization of record-keeping through the use of cryptography.
Currently it is associated with financial applications but it has numerous other applications.
- Fact: Blockchain has transactions that are possible in various sectors which include supply chain solutions, identification, voting, and identification solutions.
Conclusion
Today, blockchain has become an innovator in the way that things are protected on the World Wide Web. It is almost as if there is a very heavy lock on the digital platform that may just be slightly hard to open. New technology, including blockchain in cybersecurity, is assisting us in protecting our important items and cash in sectors we could not do in the past. It achieves this by passing information through many computers and thereby making it hard to get a hold of or to manipulate. It also enables one to watch, and these practices help in avoiding cases of the ‘’bad people’’ to perpetrate their ill deeds.
But blockchain isn’t perfect. Although it is functional, it has those small problems that need to be solved or fixed. Nonetheless, as the threats rise, digital space, moreover, with the assistance of blockchain in cybersecurity, offers a reasonable way to oppose them. It is assisting to create better conditions on the internet where one can freely participate in actions without being afraid of pirates or robbers. In the long run, this should make the internet considerably safer for all people with the aid of this technology.






