Digital transformation is defined as the process of incorporating digital technologies into most, if not all, aspects of a company’s operations, thereby altering how that firm serves its customers. Cybersecurity in the age of digital transformation affects a range of technologies such as cloud computing, artificial intelligence, big data, and IoT.
The Impact of Digital Transformation on Businesses is Large
- Enhanced Efficiency: Minimizing the use of manpower in some operations makes them efficient since fewer people are involved, hence more production.
- Improved Customer Experience: Other techniques make for one-on-one contacts and quick service which improves loyalty among consumers.
- Data-Driven Decision Making: The ability to use real-time data for analysis thus signifies that there is a considerable opportunity to make up right decisions, change strategies within the shortest time, and explore new markets.
- Innovation and Agility: Adopting ICT facilitates the development of the corporate culture of innovation which allows an organization to quickly adapt to emerging market needs and competitive pressures.
Importance of Cybersecurity in the Context of Rapid Technological Advancements
As the business undergoes a digital transformation the idea of cyber security cannot be underrated.
As organizations integrate technology into the execution of their functions, systems become prone to cyber attacks requiring sound measures in cybersecurity.
Key reasons for prioritizing cybersecurity include:
- Protection of Sensitive Data: Business entities deal with large volumes of customers’ information, financial details, and proprietary information. Cybersecurity protects this data from being hacked or otherwise stolen.
- Maintaining Trust and Reputation: A single leakage of data can do tremendous harm both to the company and to its clientele, thus customers’ trust can be easily undermined. Adequate measures when it comes to cybersecurity are useful in ensuring that the confidence of the stakeholders is maintained.
- Regulatory Compliance: Particularly, numerous fields are confined by strict legislation on data protection. The fact is that cybersecurity measures help to prevent violations of legislation, including laws on the protection of personal data, such as GDPR, HIPAA, PCI-DSS, and, therefore, eliminate potential fines and legal consequences.
- Business Continuity: Cybercrimes pose a lot of risks including loss of functions, and considerable monetary damages. Adopting good measures enhances the probability of not being attacked and hence sustaining the organizations business.
Brief Mention of The Evolving Threat Landscape
The threat environment is rather dynamic, and new threats occur due to the constant development of new technologies and the introduction of new products by various criminals. Cyber threats now encompass a wide range of tactics and strategies, including
- Ransomware Attacks: Holders of ransomware cyber-attacks gained access to the organizational data and encrypted it to force the organization to pay a certain amount for its release, especially targeting the sectors of critical infrastructure as well as healthcare.
- Phishing Scams: Scams are threats, that obtain users’ personal information or make them install viruses through false messages, so human error remains a weakness.
- Advanced Persistent Threats (APTs): Cyber Espionage are sustained strategy, whereby professional hackers sneak into an organization’s networks to steal information or interrupt network operations.
- IoT Vulnerabilities: The entrance of many connected devices poses high risks because most IoT devices continue to have little to no security.
In this dynamic environment, businesses must remain vigilant and proactive in their cybersecurity efforts, continuously adapting to emerging threats and ensuring their defenses are robust enough to protect against potential attacks.

- Lightning-fast speeds to browse without lag
- Servers in 105+ countries around the globe
- Military-grade security to stay safe online
- Try it risk-free with its money-back guarantee
- Native apps for all major devices
Understanding Digital Transformation

Digital transformation is an organizational-wide process of utilizing digital technologies to transform an organization’s fundamental processes and the methods through which they deliver value to customers.
What makes this transition not a purely technical one is that it entails a culture change based on the idea that organizations must always question the existing paradigm, probe, and innovate for success in the contemporary market.
Digital transformation refers to a wide spectrum of technology solutions and processes that comprise cloud solutions, artificial intelligence, big data analysis, and IoT.
Lastly, it is focused on reducing costs and increasing productivity, optimizing clients’ satisfaction, and fostering innovation within the company.
Key Drivers of Digital Transformation
- Remote Work: The global pandemic led to actions that force employees to work from home, because of this, companies invested in effective tools and application of technology. This shift has exposed the need for safe and effective methods of conducting business remotely.
- Cloud Adoption: Cloud computing services augment demands and require the right selection of service arrangements for meeting needs for growth, decreasing IT costs, and increasing the availability of data and applications. Through cloud computing security, organizations can accommodate the working-from-home model and benefit from fast-paced innovation.
- AI Integration: AI is revolutionizing the functioning of business by enabling automation, improving decision-making, and delivering individualized customer’ services. AI customers useful enterprising knowledge that would allow the organization to comprehend customer trends and operate more efficiently.
- Customer Expectations: As the knowledge of using technology of the consumers rises, their expectations of the program’s continuity and relevance also rise. Managers are expected to address these expectations by integrating technologies into the operations of organizations to more effectively engage the clients as well as create value.
The Role of Technology in Reshaping Business Models and Processes
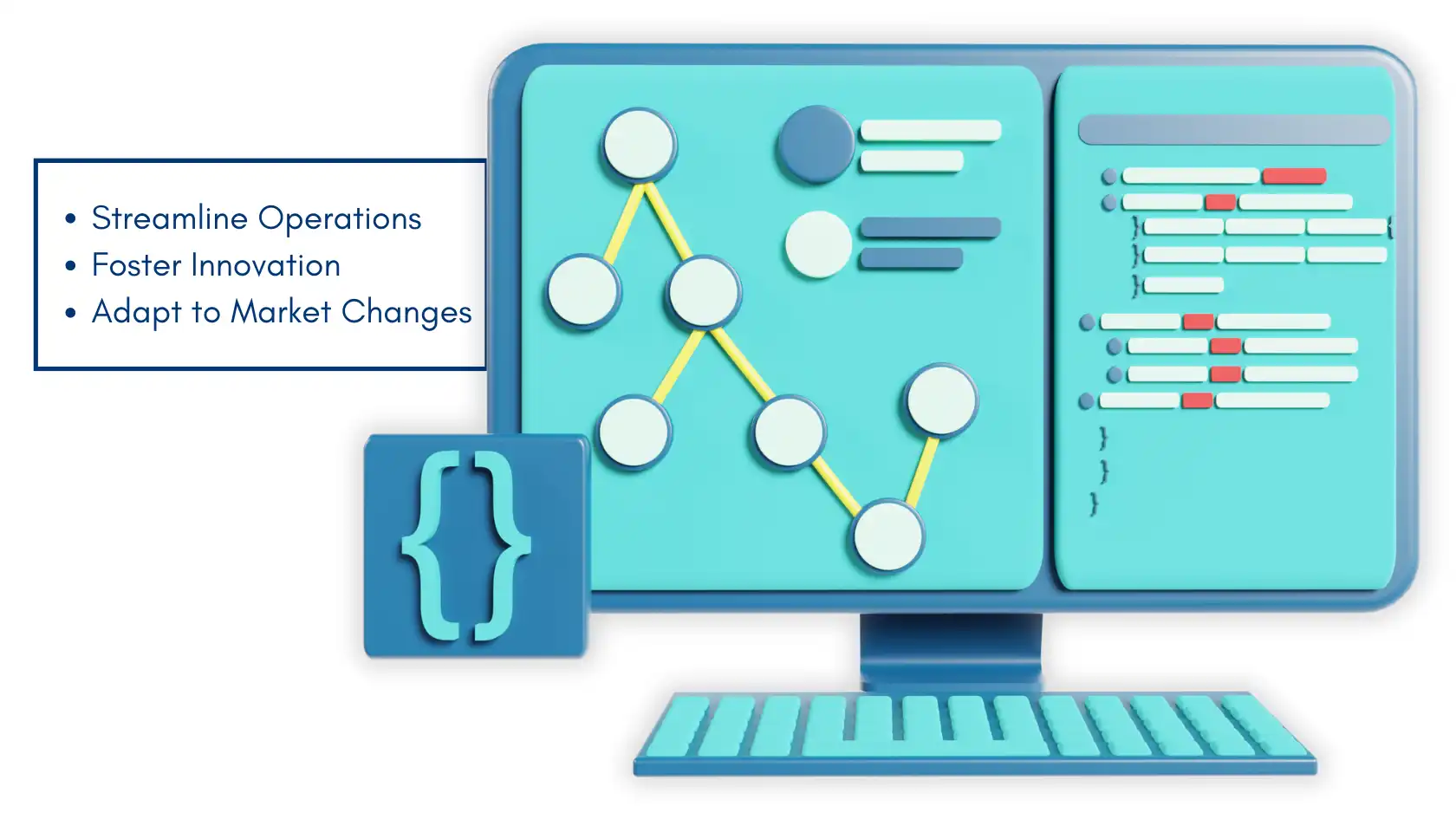
Thus it can be denoted that technology can bear significant importance while bringing changes in business models and business processes. It enables organizations to:
- Streamline Operations: Computerization also helps to minimize the time, effort, and errors that are usually made during a manual task so that the employees can work on more complex tasks. This will have the following effects and these include increased efficiency and productivity in an organization.
- Enhance Customer Engagement: Technology employed in the modern organization requires incorporating online communication tools as a way of nurturing business relationships with the clients and in return quickly attending to their needs. It helps in the satisfaction of the customers thus making them loyal.
- Foster Innovation: Technology enables organizations to innovate or test fresh new ideas or conditions in business. If information is analyzed and the new technology is embraced, companies will be in a position to discover new markets to plunge into and solutions to present to the market.
- Adapt to Market Changes: This shows why being adaptable in the market helps an organization because items that are popular today may not be popular tomorrow. Digital transformation prepares organizations for changes and events, making them ready to act on them, and capture value.
All in all, they have an understanding of digital transformation as a complex and comprehensive process influenced by technological innovations, customers’ expectations, and the organization’s concerns about efficiency.
Modernization of organizations means increased competitiveness, better customer experience, and sustainable development in the context of digitalization.
The Evolving Cybersecurity Landscape

Overview of Current Cybersecurity Threats
Modern threats can be listed as complex threats that contain various dangers for organizations Today. Key threats include:
- Ransomware: Hackers steal full data sets and hold data for ransom and this is mostly directed to core facilities, organizations, and other institutions. It has been noticed that ransomware attacks are frequent and expensive, and the cybercriminal uses different levels of approach.
- Data Breaches: These are some of the consequences that may occur when unauthorized personnel accesses the company’s information which is quite devastating to the financial status and reputation of the company. Most of the attacks happen because of weak spots in a system or misrepresentations of the authorities, like phishing.
- Phishing: This is a popular trend where those behind the crime create fake emails or sites that look like those of banks, social sites, or other important areas of an organization to get the targets to give out their passwords, etc. Stay safe from cyber threats, particularly phishing attacks, which have continued to change and become more complex.
- Advanced Persistent Threats (APTs): These are sustained and carefully planned cyber aggressions and they are always by a state actor to penetrate a network to steal information or hamper activities. APTs can be dormant for a long time which makes them quite lethal.
How Digital Transformation Has Expanded the Attack Surface for Organizations
The process of digital transformation has opened up rich avenues for cyber attackers that were not existent before. Key factors include:
- Increased Connectivity: With organizations adopting cloud services and IoT devices the organization has many more entry points for attacks. Each linked device or application can be a threat source.
- Remote Work: Due to COVID-19 restrictions, companies are forced to work remotely which causes VPNs and cloud tools usage. Despite these technologies’ increase in flexibility, they bring various risks in their wake if not well protected.
- Cloud Migration: Lifting the assets to the cloud translates to better efficiency standards, yet it makes organizations vulnerable to cloud-based risks. Loopholes and low protection prevents the data from being secured thus allowing unauthorized access to the data.
- Third-Party Risks: Many companies outsource different services from third-party vendors – this can become a problem if the latter do not have proper security measures in place. These vulnerabilities can be exploited by supply chain attacks to compromise the needed data.
The Need for Cybersecurity Transformation

Uninterrupted, high-speed browsing, zero logs so your online activity is always private.
Over 7000 people checked out NordVPN in the last month
Why Traditional Cybersecurity Measures Are Insufficient in a Digital-First World
The concepts of keeping the organization’s security perimeter intact in a digital setting are no longer adequate to be relied on with perimeter-based tools like firewalls and best antivirus programs.
During the transformation process, organizations have opened new attack vectors by using cloud solutions, cooperating and working remotely, and connecting all kinds of systems.
Most of the cyber threats are evolving and applying new strategies that can evade standard security barriers.
Furthermore, technological advancement occurs at an unprecedented rate, necessitating proactive and continuous response mechanisms for security that are not just an add-on to the organizations’ planning but are inherent in their technological solutions.
The Shift from Viewing Cybersecurity as a Cost Center to a Business Enabler
Cyber security plays a major role in organizations, up to this point in time, it has mainly been regarded as a cost discipline, which negates the flexibility that is required for any organization to capture new and exciting markets.
However, as is the case with other opportunities in the digital terrain, organizational leaders are slowly coming to appreciate that secure operation is the foundation for achieving business objectives.
Cyber security framework is important not just for shielding organizations’ assets and data, but also for creating confidence in customers and partners.
This makes cybersecurity strategic for any business since it acts as a business enabler and a way through which the organization can show its dedication in matters concerning data protection and privacy.
It shifts the focus toward investing in cybersecurity programs that support an organization’s objectives and its digital agenda.
The Importance of Integrating Cybersecurity into the Digital Transformation Strategy
The management of cybersecurity needs to be incorporated into the plan of digital transformation so that security solutions are consistent with organizational goals.
With the promotion of new technologies and approaches in various organizations, there should be a more inclined focus to ensure the security aspects are observed and achieved from the initial stage properly.
This incorporates measures such as addressing security as an in-built characteristic that is added into the creation and building of applications and systems.
In addition, it is possible to improve security in a digital environment by applying certain principles, for example, zero trust, according to which access is granted based on constant checks.
In other words, when companies ensure security as a concept of their digital strategies, they can safeguard their valuables, meet compliance requirements, and earn their customers’ trust, all these being key factors in achieving long-term success in today’s interconnected economy.
Integrating cybersecurity in digital transformation is essential to align security measures with technological advancements and organizational goals.
Key Principles of Cybersecurity in Digital Transformation
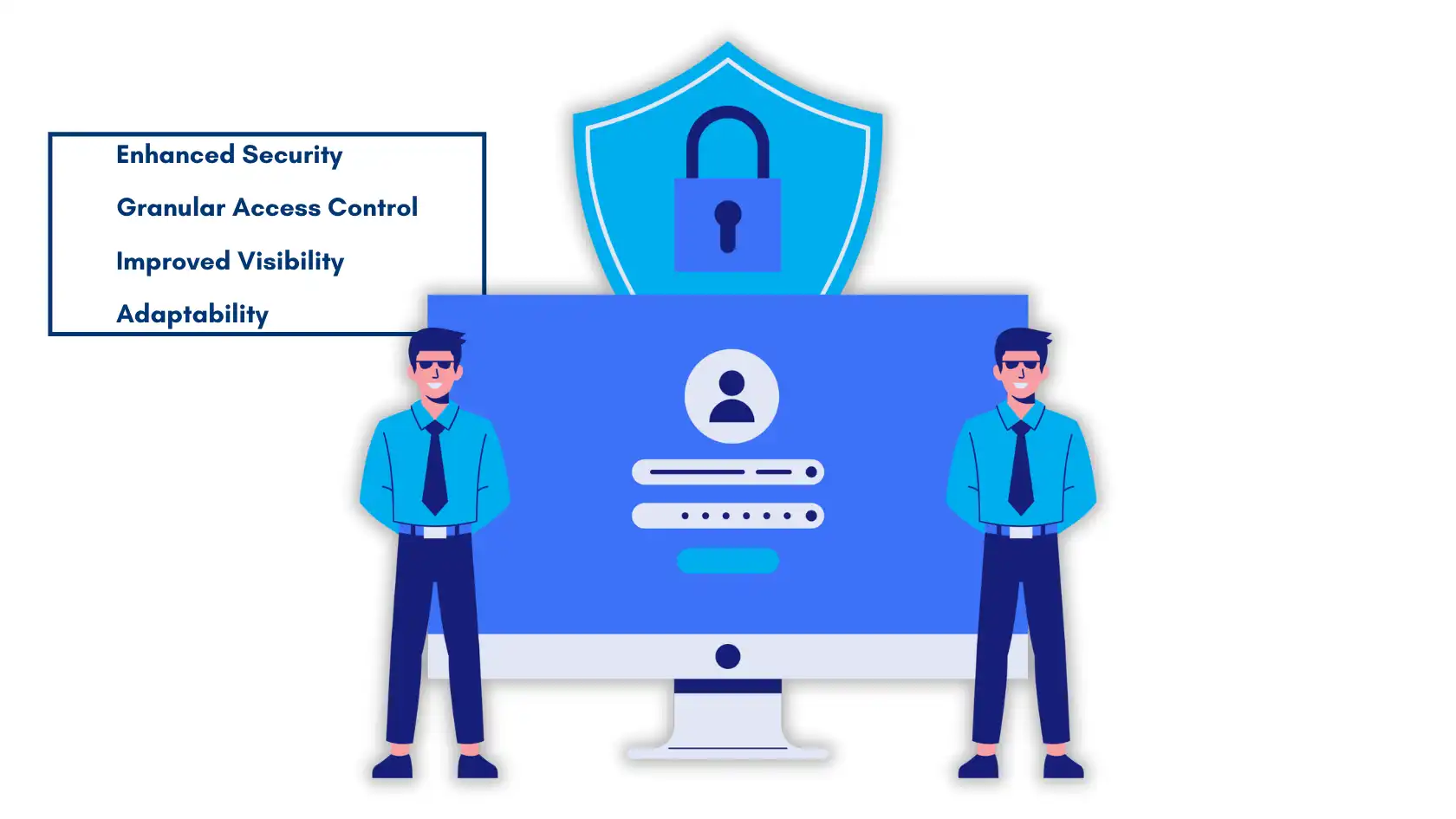
Zero Trust Architecture: Explanation and Benefits of Adopting a Zero-Trust Model
ZTA is also a security model which translates to ‘’never trust, always verify’’; this means that it is an approach that holds that there could be threats originating internally or externally and, as such, no user or device within it should be trusted no matter the position of the device.
Benefits of adopting a Zero Trust model include:
- Enhanced Security: These are achieved by providing constant user identity and device health checks hence limiting the attack surface that ZTA has to mitigate.
- Granular Access Control: They have provided access to shared files and others are allowed on the terms of least privilege, meaning they are allowed only permission to complete their task. This happens in lateral movement within the network if an account is compromised in some way.
- Improved Visibility: The way ZTA works is it continuously monitors the activities of the users and alerts the organization in cases of probable threats.
- Adaptability: It is also responsive to changing threats and business conditions meaning it is applicable in organizations that are in the process of transforming digitally.
Secure by Design: Importance of Embedding Security into the Development Lifecycle
Secure by Design is a principle suggesting that security solutions have to be integrated with the program from the earliest stages of the software development lifecycle (SDLC).
Such a strategy means that security is not something that must be added at the end of the development process but a basic component of product design.
Importance of embedding security into the development lifecycle includes:
- Early Detection of Vulnerabilities: This way, the organizations apply security measures during the development of the systems to find out the weaknesses and plug them before major exploits can be made.
- Cost-Effectiveness: Securing an application before it is deployed to production is always cheaper than doing it while in service as penetrations in the latter can cost lots of money and harm the image of the company.
- Compliance and Regulatory Adherence: He fellows many industrial standards for managing data and many industries have strict compliance requirements that need to be followed in this regard. Building security in also means that this goal becomes incorporated into the development life cycle and applications are delivered to conform to these standards.
- Enhanced User Trust: Web applications that are designed with security objectives to be achieved end up being effective because they build trust with the people using them concerning their information.
Automation and AI: How Automation and AI Can Enhance Threat Detection and Response
Automation of cybersecurity procedures, along with the usage of artificial intelligence, also fortifies an organization’s capability in threat identification and management.
Key ways automation and AI enhance threat detection and response include:
- Real-Time Threat Detection: Advances in machine learning algorithms will be towards a system that will be able to parse large volumes of event feeds in real time and discover characteristics of an event that suggests a cyber threat. These enable fast responses in the case of probable occurrences of an incident.
- Automated Response Mechanisms: One of the effects of integration of automation is that most of the general procedures in response to threats can be executed automatically, thus eliminating the need for people and hence minimizing response time.
- Predictive Analytics: AI also can predict threats in the future using existing information and shifts that may be experienced by the organizations’ worth Defending itself.
- Resource Optimization: Automation of these tasks free up the talent’s time for more pressing matters and can enhance the organization’s security posture overall.
To conclude, the principles of implementing Zero Trust Architecture, integration of security from the development phase, and the use of automation and Artificial Intelligence are also viable trends to improve cybersecurity towards the background of digital transformation.
Such tactics not only guard against emerging risks that may affect business entities but also allow for development and expansion within the safety bubble.
Challenges in Cybersecurity During Digital Transformation
Common Obstacles Organizations Face
Organizations undergoing digital transformation encounter several significant challenges in cybersecurity, including:
- Talent Shortages: The recruitment problem is exacerbated by the fact that there is a severe global deficiency of talented cybersecurity workers, which hinders organizations from creating competent security teams. This talent gap results in poor security and enhances specific vulnerabilities into cyber risks to an entity.
- Legacy Systems: Most organizations are still using old outdated legacy systems that cannot meet modern security problems. Most of these systems may not have critical security measures put in place to protect them from attacks or even integration with other new modern applications.
- Increased Complexity: The use of multiple forms of computing technologies, namely cloud services, IoT devices, and third-party applications introduce multiple complexities in an organization’s IT structure. This is the reason why many organizations are struggling to deal with security weaknesses since it is heavily influenced.
- Cultural Resistance: They remain loyal to the procedures that worked previously and that is why they can negatively respond to organizational change especially when it comes to incorporating security measures. Such resistance can slow down the optimal enforcement of ideal cybersecurity measures.
Strategies for Overcoming These Challenges
These are the challenges of cybersecurity during digital transformation, organizations can implement several strategies:
- Invest in Training and Development: To overcome the talent gap organizations are made to focus on the training and development of their existing employees. Training existing employees is beneficial as it improves how employees in organizations recognize and address cyber threats.
- Modernized Legacy Systems: There is a general idea of moving decades-old systems progressively to new modern systems that are less prone to exploits. The management of an organization should first evaluate the current network environment in place and then focus on enhancing the level of security in the various technologies in place.
- Adopt a Holistic Security Approach: About the management of complexity, the following measures should be taken – the organization should adopt and pursue a coherent multi-layered cybersecurity policy throughout the whole organization – people, processes, and technologies.
- Foster a Security-First Culture: As for the human risks, it is crucial to establish a culture of security awareness that may reduce possible negative outcomes. Managers and executors of organizations should provide more attention to data protection and introduce requirements for reporting actions of different malicious intent.
FAQs About Cybersecurity in The Era of Digital Transformation
What are the threat vectors to cybersecurity during digital transformation ?
Shortage of talents, outdated technology infrastructure, expanding application landscape, and organizational conformity towards info sec changes.
Why should the protection of an organization’s information assets not be viewed but as a way to provide advantage ?
Cybersecurity means trust, innovation, and good IT transformation in organizations and industries.
How does AI bolster cybersecurity in the age of digitally enabled systems ?
AI can identify threats, and notice new forms of attacks which makes security an evolutionary process.
Conclusion
In the age of digital transformation, cybersecurity is paramount for protecting sensitive data and maintaining trust.
Organizations must evolve their security strategies to address expanding attack surfaces and sophisticated threats.
Embracing principles like Zero Trust and Secure by Design enhances resilience against cyber risks. Moreover, integrating cybersecurity into business operations positions it as a value enabler rather than a cost center.
As digital technologies continue to reshape industries, proactive cybersecurity measures are essential for safeguarding assets and ensuring compliance.
Ultimately, a robust cybersecurity posture not only protects organizations but also fosters innovation and drives sustainable growth in a digital-first world.






